Blog
How To Make Reporting a Phish So Easy Even Your Busiest Execs Will Do It
Tue, 02/13/2018
Frustrating, isn't it?
You design a powerful anti-phishing program, secure funding from your executive board, provide world-class training. You do everything right…
Oh, your users are probably spotting phishing emails. After all, they've engaged with the training, and seem to be taking it seriously.
But no matter how many times you remind them, they just won't report those phishing emails.
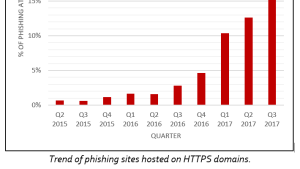
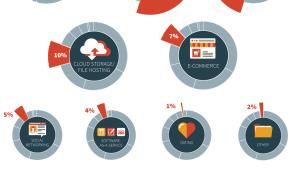
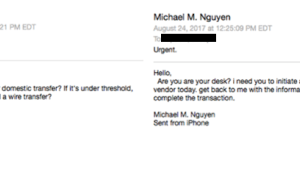
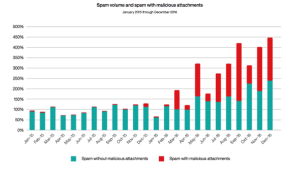
...