Blog
COVID Phishing Update - Coronavirus wants your Bonus, too
By Jessica Ryan on Thu, 03/19/2020
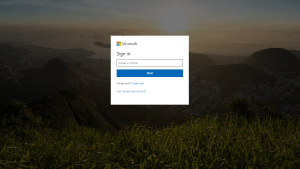
A few weeks ago we noted some early examples of Coronavirus phishing campaigns. Since then, the pandemic has spread and we've seen a dramatic uptick in COVID-19-themed malicious activity, with everything from domain registration to phishing emails and even malware campaigns. Going forward, we will be publishing more examples as we find additional methods cybercriminals are using to exploit the...
e97e.png)





1a90.png)
6784.png)
2306.png)





87e4.png)
9bcf.png)