 It’s a sobering moment.
It’s a sobering moment.
You work long and hard to prepare your users. You train them. You test them. And over time, you see amazing results.
But then it happens.
Just when you think your users are becoming rockstars at identifying phishing emails, threat actors throw a new tactic at you… and everybody falls for it.
Of course, this isn’t a new story. Threat actors constantly update their tactics to maximize the impact of their phishing campaigns, so it shouldn’t be a surprise when something different comes along.
Spear phishing is comfortably the biggest cyber threat to most organizations. Why? Because exploiting people is almost always easier than exploiting technology.
To find out how and why your employees will be exposed to social engineering attacks, and what you can do about it, register for our free on-demand webinar: Why People Are Your Network's Greatest Vulnerability.
The Holiday Effect
In our recently published 2017 Phishing Trends and Intelligence Report, we highlight the impact of what we call the ‘Brexit Effect’.
Historically we’re used to seeing significant increases in holiday themed attacks during the Christmas period. In recent years, we've also observed an increase in attacks based on current events.
In 2016, the total volume of phishing attacks targeting British organizations fell by 23 percent compared to 2015. But during May and June, leading up to the historic Brexit vote, there was a massive spike. The number of attacks observed during these two months was almost double the average for the rest of the year.
And this is far from an isolated incident. In recent years, threat actors have consistently used the uncertainty and anxiety surrounding current events to increase the efficacy of their phishing campaigns. The more significant and divisive the event, the more likely targets are to click.
The Valentine’s Day Phish
To examine the power of holiday themed phishing attacks, we decided to create one of our own and test it on some of our Phishing Awareness Training customers. We created a Valentine's Day themed phishing simulation in February, and used it to test a subset of our astute, security conscious customer base.
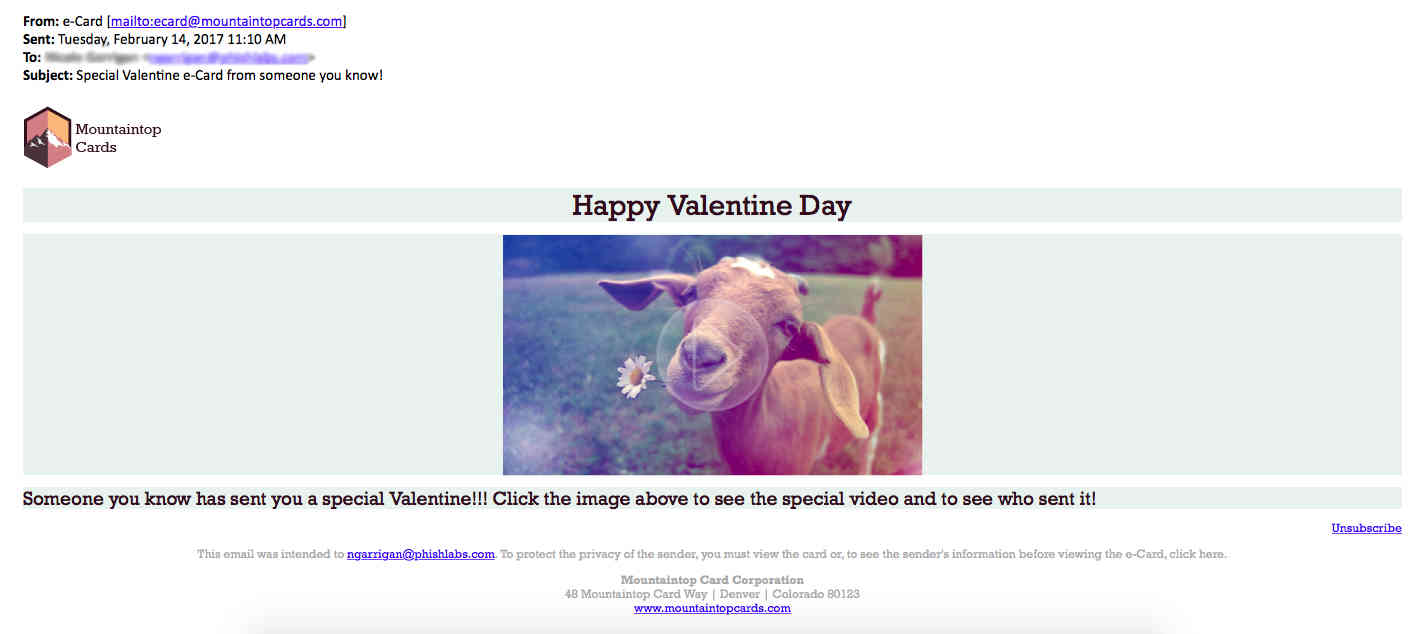
Nothing too complex, clearly, but as far as mass phish go this is more advanced than many. The sender, [email protected], is plausible, and while the language used doesn’t hold up to huge amounts of scrutiny, the idea that somebody has sent a Valentine’s video is certainly believable. The simulation also includes all the standard 'unsubscribe' text users would expect to see in this type of email.
To test how people would react to our simulation, we sent it to 14,720 users across the financial services, healthcare, and legal industries. Since these users were spread across a number of client organizations, all of which have been employing our managed EDT services for different lengths of time, levels of training varied significantly.
With that said, all users had received at least some level of phishing awareness training, and many could be considered advanced users.
So how did they do? Here are the results by industry:
| Failed | Reported | No Action | |
| Financial Services | 17% | 34% | 51% |
| Healthcare | 30% | 24% | 46% |
| Law | 45% | 0% | 55% |
And on the face of it, this doesn’t seem too bad… until you consider two things:
- The average failure rate for non-trained users is around 30 percent
- Users at every single organization failed at a much higher rate than normal
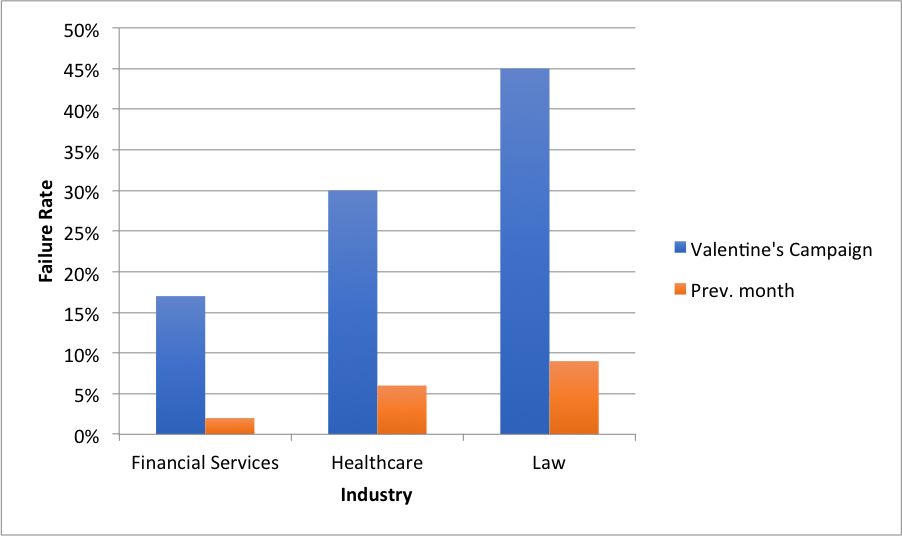 Failure rate by industry: Valentine's campaign vs. previous month
Failure rate by industry: Valentine's campaign vs. previous month
Our of our financial clients, for example, had a failure rate of just one percent in January, well below the 15 percent failure rate for this campaign. Similarly, one of our healthcare clients had a failure rate of just six percent in the previous month, compared to 32 percent for the Valentine’s Day simulation.
So what makes this simulation so much more powerful than the rest? Well, for a start, people expect to receive these types of emails. In recent years there has been an explosion of online card websites, and it’s perfectly plausible for most people to receive them.
But there’s more to it than that. This simulation combines the familiarity of holiday themed emails with every BuzzFeed writer’s favorite emotion: Curiosity.
You know what I’m talking about. All those clickbait links on Facebook with titles like “At first I was concerned about
Well, this phishing simulation was our version of clickbait. The email doesn’t say who has sent the recipient a Valentine’s Day card. Is it their significant other? A secret office admirer? Their mother?
One of the most powerful things about holiday or current events themed phishing campaigns is that there is already plenty of emotion surrounding the topic. Once you add in an extra layer of intrigue, no matter how obvious, you have an extremely powerful tool on your hands.
Not Losing Isn’t the Same as Winning
There’s one more aspect of this campaign that we’d like to highlight. We’ve seen that failure rates for the Valentine’s Day phish were well above normal, but how about tracking the positive responses?
| Failed | Reported | No Action | |
| Financial Services | 17% | 34% | 51% |
| Healthcare | 30% | 24% | 46% |
| Law | 45% | 0% | 55% |
In total, 73 percent of all recipients opted not to click on our phishing simulation.
But let’s not start celebrating just yet. Of the users who didn’t click through, the majority simply ignored the email, with only 26 percent of total recipients choosing to report it as malicious.
And that’s a problem. As with any phishing campaign, a single click can potentially lead to a data breach, and all the cost and disruption that goes along with it. When a particularly powerful campaign comes along, the increased number of clicks dramatically increases the chance that serious damage or compromise will occur.
In this case, of the 14,270 users tested, 3,815 failed our simulation. If this were a real phishing campaigns, that would give our hypothetical threat actor 3,815 chances to gain a foothold inside one of our clients' networks.
In these instances, it’s vital that those users who do identify phishing emails as malicious take a few seconds to click ‘report’. When they have this type of early warning, security personnel can take steps to quarantine the email before other users are exposed to it, as well as updating the organization’s spam filter to block similar emails in the future.
But if phishing emails aren’t reported in a timely fashion, it’s highly unlikely they’ll be able to complete these steps before an unwitting or distracted user inadvertently puts the organization at risk.
Reinforcing the Message
So what can we learn from this experiment?
In this simulation, we intentionally exposed users at a range of client companies to a more sophisticated phishing email than most of them were used to seeing. You’ll notice from the earlier tables that a few of our clients still managed to achieve high levels of success, but the others, who have been with us for less time, really struggled.
But that’s not a bad thing. Many of these users had likely never seen a holiday themed phishing email before, and consequently had no idea such a thing existed. Now that they have, and they’ve received the follow-up training, they’ll have a much higher chance of identifying real holiday themed phishing emails in the future.
And, at its heart, that’s what powerful security awareness training is all about. If we simply provided training, without ever testing users’ ability levels, our clients would have no idea if their users had improved. But because we provide both, along with follow-up training for users who ‘fail’ a simulation, our clients are able to track improvements over time.
In the end, no matter how good your technical controls are, some phishing emails will make it through. And at that point, your users are the only remaining line of defense.
Security Awareness Training Buyer's Guide
No matter how much you spend on security products, some phishing emails will always make it into user inboxes. From there, you're at the mercy of your users.
The right SAT program can take your users from security liability to security MVPs.
Read this white paper to learn:
- How to plan and develop an SAT program
- What SAT options are available, and the pros and cons of each approach
- What to look for in a vendor-bought SAT program
- The key points every SAT program should address
- How to measure the success of your SAT program