Blog
Social Media as a Threat Channel
Thu, 04/21/2022
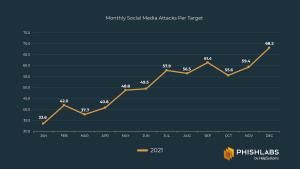
Social media offers an important outline for people of all ages and walks of life to connect, share life experiences and post pictures of their breakfast. But oversharing - or not being wary of impostors - can lead to serious compromises in personal and professional security. In a press release on the report's findings, Phishlabs “enterprises must broaden their line of defense [in 2022,]...