Social media is rapidly becoming the preferred online channel for threat actors. Almost four billion people use some form of social media, and organizations are increasingly reliant on company pages, executive presence, and positive customer interaction to build a strong brand. As a result, a malicious post or tweet can cause irreversible damage to an enterprise.
Last year, 53% of all social media accounts were reported as fraudulent. The volume of data on social networks makes identifying real threats to your organization tedious and time-consuming. In order to protect against bots or suspicious activity on these platforms, organizations must have strong social media protection programs in place and defined criteria to curate intelligence.
The overwhelming volume of data on social media requires security teams enact processes that will streamline response times to suspicious activity and reduce the lifespan of threats. In order to sufficiently gather data, they must first search all social platforms that apply to their organization. Doing this in a timely and effective manner requires a combination of machine processing and human analysis.
There are four components to turning social media data into actionable intelligence:
- Classify the threat
- Determine its severity
- Eliminate false positives
- Add context
The broad scope of information present on social media means security teams are often burdened with high volumes of potential threats that turn out to be benign. To reduce this noise, potential threats should be classified using relevant algorithms and keywords to quickly find targeted references. An example of this is defined criteria such as brand activity or fuzzy matching.
Context must also be given to each threat as it applies to your business in order to assess whether or not it is a real risk. Human analysis ensures legitimate threats won't be neglected or benign activity misinterpreted.
In order to achieve alignment, analysts must learn the specific needs of their organization as well as social media. This ensures each threat is correctly identified, its relevance confirmed, and severity established. Additionally, any changing business priorities and context must be applied through expert analysis before determining how to respond the threat.
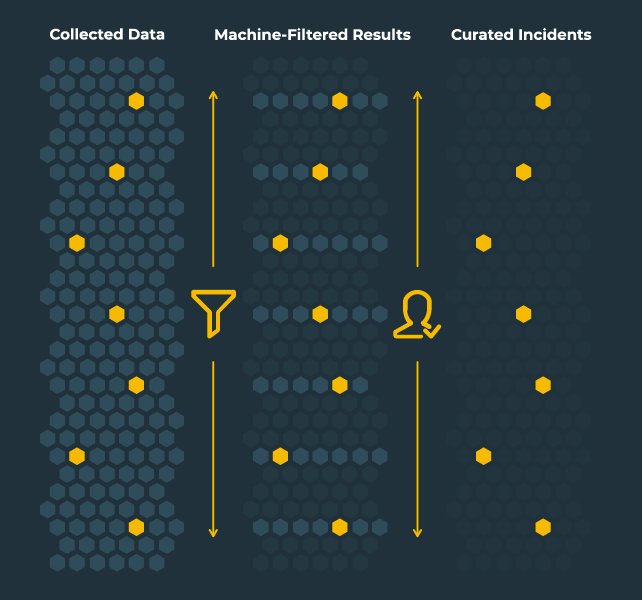
The dramatic increase in social media abuse means organizations must be able to identify a variety of threat types spanning an array of different social platforms. Successfully protecting against these threats requires social media threat monitoring and broad collection that is paired with a tuned curation process. This will minimize false positives and lead to high-fidelity results that can be swiftly acted upon.
Without a combination of machine processing to comb relevant channels, and expert analysis to add context, security teams cannot efficiently identify and mitigate the threats most significant to their organization. PhishLabs Social Media Protection proactively protects enterprises from threats on social media.
To learn more about navigating social media threats, download our playbook.
Additional Resources:
