During a recent analysis of a business email compromise (BEC) scam, we observed a lure attempting to install the Olympic Vision Keylogger. Further research determined that this keylogger and the accompanying Olympic Vision Crypter were used in a larger campaign, targeting multiple organizations using a variety of different lures, including invoice lures and shipment confirmation lures. This campaign appears to be originating out of South Africa, utilizing both maliciously registered free domains as well as compromised domains.
Keylogger software is an attractive tool for threat actors to use in spear phishing/business email compromise scams as it can provide insight regarding internal procedures, while also logging access credentials that can be used to pivot within an organization. Even if the employee who is originally targeted does not have access to sensitive or privileged information within the organization, intelligence can be garnered about operations of the organization that can be used to then target persons higher in the hierarchical structure.
Olympic Vision Keylogger also comes with an attractive price tag. Cybercriminals can purchase a keylogger subscription for as little as $15 and a Crypter subscription for only $17.
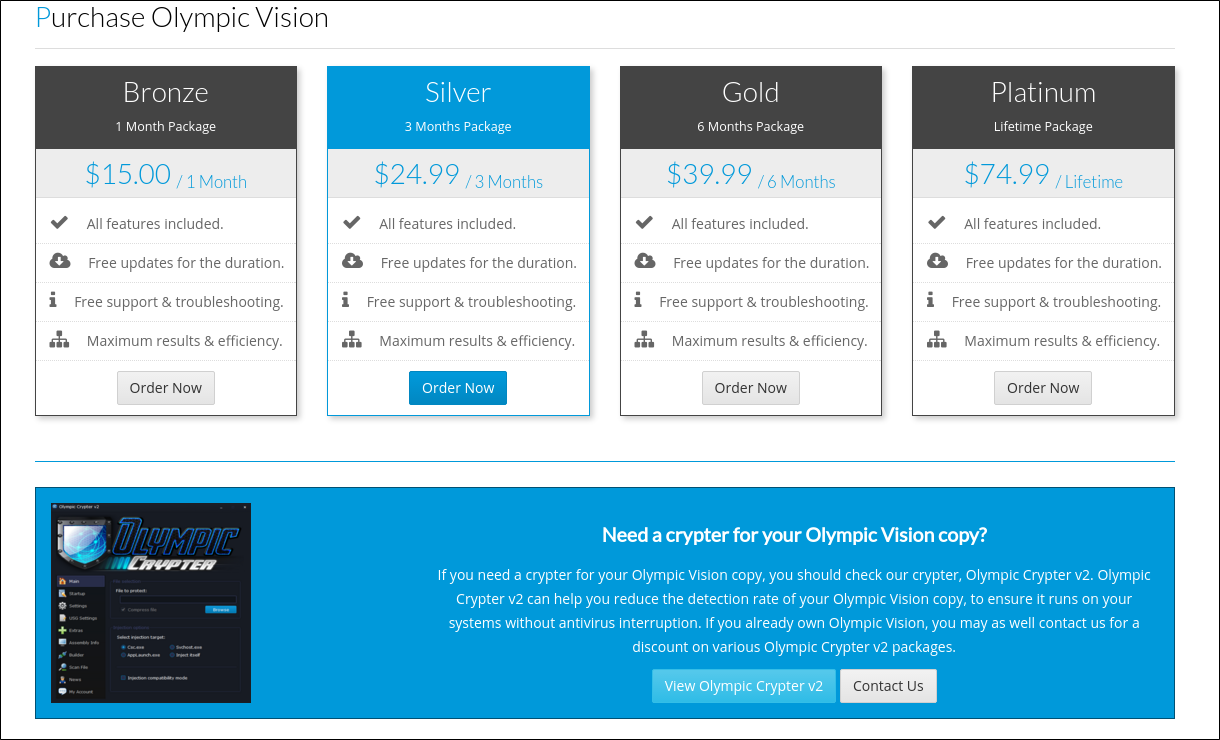
Olympic Vision Pricing Schedule
With the FBI reporting that BEC scam perpetrators have skimmed over $2.3 billion since October of 2013, these small fees seem like a sound investment for the attacker to augment the chances of success.
The attack analyzed for this post contained a lure indicating that a purchase order was attached and the purchasing manager will be visiting the victim institution “next month to close the deal."
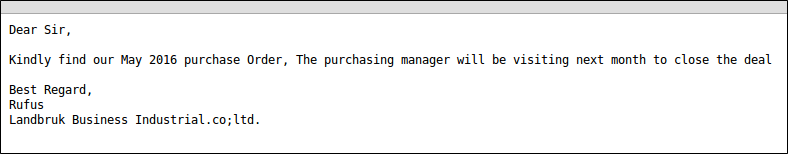
“Purchase Order" Lure Email
Because of the way the lure is written, it could have been sent to any employee of the company, who by habit would forward the purchase order to the person responsible for handling such requests. Once received, should an employee open the “purchase order" attached to the email, the keylogger would be installed on their computer.
The Olympic Vision Keylogger has the capacity to route stolen information to the attacker via email, FTP, or HTTP. After the keylogger is configured and built, it can then be passed through Olympic Vision's custom crypter which claims to make the binary fully undetectable by antivirus vendors. The Olympic Vision Keylogger is capable of gathering and exfiltrating system data, keystrokes, clipboard contents, screenshots, and credentials stored by browsers, email, FTP, and instant messaging clients.

Olympic Vision Builder

Olympic Crypter
The malware is written in obfuscated .NET code, so it requires the .NET framework to be active in order to run. Should .NET not be active at the time of infection, an error pop-up window is produced and the victim is directed to the Microsoft page which contains instructions for enabling .NET in Windows. Assuming the .NET framework is available on the victim's machine, the sample runs and injects itself into a svchost.exe process, and then spawns cmd.exe multiple times in order to execute reg.exe to edit the Windows registry.
The sample analyzed utilize free open source modules from Security Xploded, which is common for tools sold by Olympic Vision (also known as CodeLux. The Security Xploded “BrowserPasswordDump," “FTPPasswordDump," “IMPasswordDump," and “EmailPasswordDump" tools are used to log stolen information to a SQLite database, which is then exported to a .TXT file on both the local machine and on a C2 domain. These programs were found in the Modules.resources section of the sample, each packed with UPX. Once decompressed, a majority of the programs' strings can be viewed in plain text. The following screenshot shows an example of output from the “BrowserPasswordDump" module.
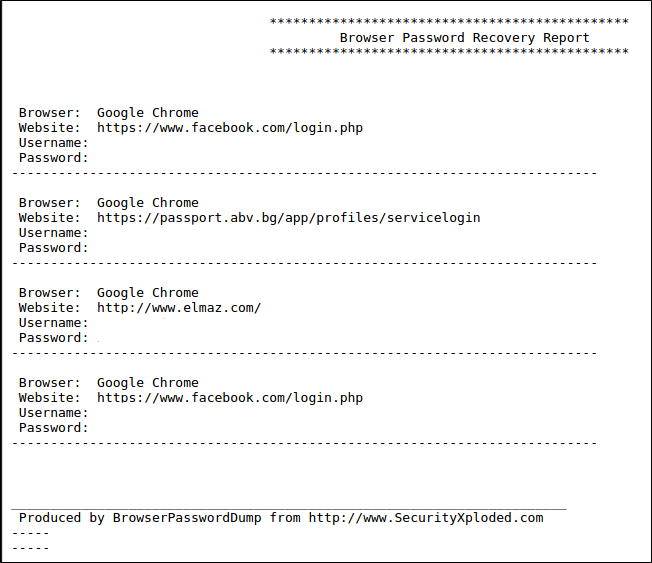
BrowserPasswordDump Module Output
Log files also store a screenshot and system information for each infected machine for tracking purposes.
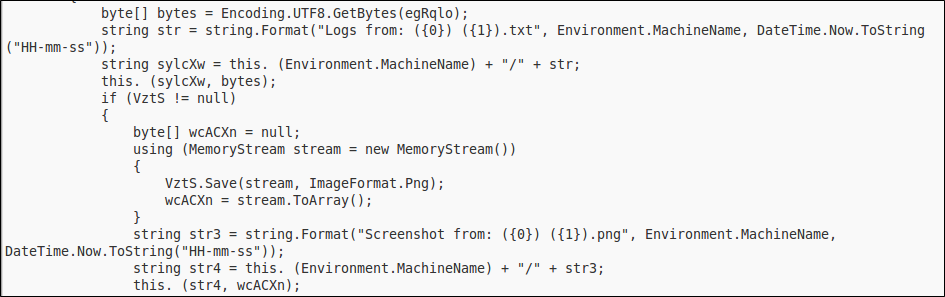
System Information Logging
Upon review of the decompiled source code, we were able to determine that the sample in question was feeding information back to the threat actor via FTP exfiltration. AES encrypted strings, as well as the related decryption key, were co-located in the Settings.resources file. The encryption code runs in Electronic Code Book (ECB) mode, which causes identical plain-text blocks to be encrypted into identical ciphertext blocks, thus allowing each block to be decrypted in the same manner. When these strings were decrypted, we were able to reveal the FTP server being used to receive the stolen credentials in this sample.
Previous research into Olympic Vision C2s completed by Trend Micro identified compromised domains utilizing the .co.za and .ng top-level domains, as well as malicious domains utilizing free domain registration services. Our additional research identified that the malicious domains were registered from South African IP addresses, leading us to attribute these scams to likely be originating from that geographic region. We also found that the threat actor's username we discovered was used on at least one other of these previously identified Olympic Vision C2s. The domain used for FTP exfiltration in our case was registered 5/9/2016, making this a more recent attack than those observed in prior discussions regarding the Olympic Vision tools, for which the domains were registered in January of this year.
Although business email compromise scams can be used to drop any type of payload on a victim's computer, the simplicity of purchasing inexpensive, pre-built tools and utilize them in a malicious nature broadens the range of potential targets. The tools and modules utilized in this attack are openly available for use and can serve legitimate purposes for security researchers and penetration testers. However, when utilized with malicious intent, the effect can be severely detrimental for the receiving party. Companies will be well served to educate their employees on how to effectively review suspicious emails and identify social engineering attempts that may appear to be coming from vendors or coworkers.
Join us for a webinar on June 22nd to discuss Spear Phishing and the Ransomware Threat.
For more on Business Email Compromise (BEC) phishing attacks and how to fight back, view our recent webinar on demand.