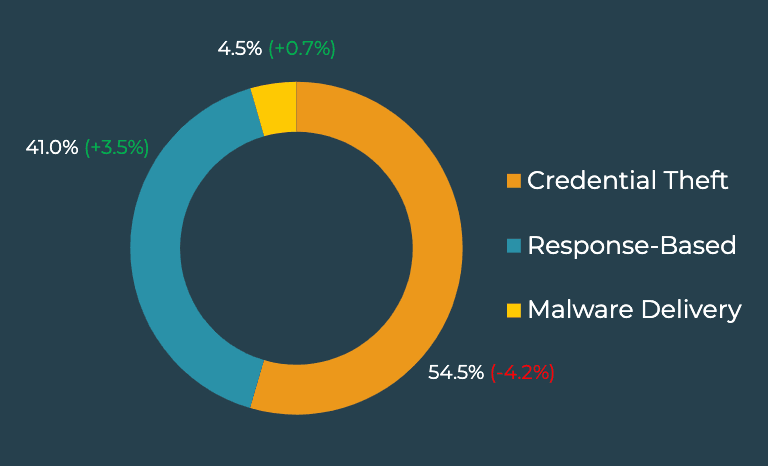
In Q2, Response-Based emails targeting corporate users reached the highest volume since 2020, according to the Agari and PhishLabs Quarterly Threat Trends & Intelligence Report. Malicious and potentially damaging emails targeting corporate inboxes have climbed to a three-quarter high, and include Response-Based scams, Credential Theft, and Malware.
Every quarter, Agari and PhishLabs analyze hundreds of thousands of phishing and social media attacks targeting enterprises, brands, and employees. In this post we discuss intelligence collected through PhishLabs’ Suspicious Email Analysis solution.
Credential Theft
In Q2, Credential Theft incidents contributed to the majority of email-based threats, representing 54.5% of volume. Although Credential Theft activity declined 4.2% from Q1, it continues to be the top email threat to corporate users.
Attacks targeting Office 365 accounts are climbing, up 17.7% compared to Q4 2021. O365 incidents represented nearly 60% of all Credential Theft phishing attacks that contained a link, reaching a six-quarter high in share and volume. Account credentials associated with collaboration applications and tools are valuable assets to criminals, who use stolen login information to access multiple machines within a network. Malicious attachments such as Docuphish made up 15% of Credential Theft attacks, declining 5.2% from Q1.
Response-Based Attacks
Advanced-Fee Scams (419) represented the top Response-Based threat-type in Q2, contributing to more than 54% of share of volume. Advanced-Fee Scams are consistently the most reported threat-type within the group and so far have increased 3.4% in 2022.
Despite demonstrating a slight decline in share, hybrid Vishing attacks were the second most reported Response-Based threat type, increasing 625% from Q1 2021 to Q2 2022. This represents a six quarter high in volume. Hybrid Vishing emails use a unique combination of email lure and mobile number within the body to convince victims to call a fake representative. Once the parties engage, the victim submits their personal information, believing it is being received by a legitimate and familiar business.
Business Email Compromise (BEC) attacks were reported more in Q2, representing 16.3% of Response-Based threats. Job Scams and Tech Support rounded out the top five, contributing to 4.8% and 0.2% of all reported attacks.
Malware Delivery
Emotet has regained its status as top payload after being disrupted in January 2020. In Q2, Emotet represented nearly 50% of reported malware volume after a 30% jump in share. Emotet has demonstrated a steady, incremental increase each month since attacks commenced in November 2021.
Former leader QBot also experienced an increase in volume, despite displaying a decline in share. Combined with Emotet reports, the two malware families contributed to more than 90% of all payload volume reported in user inboxes.
Although Bumblebee was first detected in March, it was the third most reported payload in Q2, contributing to 2.9% of attacks. Its emergence took place in the same timeframe Trickbot and BazaLoader reports dropped, raising speculation that Bumblebee was designed to replace one or both.
Email-based attacks climbed in Q2, with Credential Theft, Response-Based scams, and Malware delivery all experiencing increases in threat count. In order to protect against threats that make it past security controls and into employee inboxes, security teams should gather and analyze suspicious email and domain intelligence from a variety of sources, as well as invest in rapid and efficient remediation.
Learn more about these threats in our Quarterly Threat Trends & Intelligence Report.
