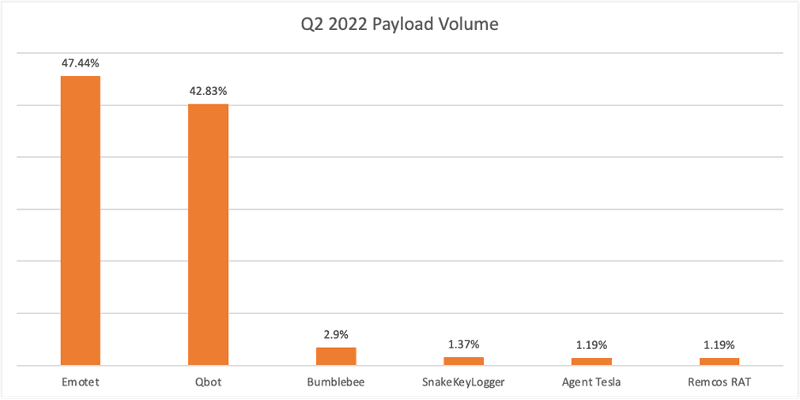
Emotet contributed to just over 47% of all attacks targeting corporate users in Q2, narrowly surpassing former leader QBot. This is the first quarter Emotet has represented the majority of payload reports since its disruption in January 2021. Together, Emotet and QBot dominated payload volume, totaling more than 90% of reported payload activity.
Malicious payloads distributed via phishing emails are the delivery method of choice for ransomware operators. PhishLabs continuously monitors payload families reported in corporate inboxes to help mitigate attacks targeting their organizations. Below are the top payload threats to enterprises in Q2.
Emotet
Emotet payloads targeting corporate inboxes contributed to 47.44% of all reported attacks in Q2. Once considered the most dangerous botnet in existence, Emotet has steadily increased in volume after rebuilding operations in November 2021.
Emotet acts as a dropper for other types of malware and is known for its novel reconnaissance and data stealing abilities. Originally developed as a banking trojan, recent upgrades to the payload showcase its advanced evasion tactics. Most notable is the malware’s distribution through OneDrive lures rather than the typical use of Word or Excel documents. This change comes as Microsoft has adjusted the default behavior of Office applications to block macros, a common way for attackers to distribute malware. Attackers have also implemented hashbusting, allowing the file hash to be different on each compromised system.
QBot
QBot contributed to 42.83% of all payload attacks in Q2, moving to the second spot among the top malware families. Previously, QBot was the top reported malware for two consecutive quarters. QBot also displayed the highest reported volume of an individual malware variety during a single quarter (Q1 2022), over the past 12 months.
QBot is a versatile banking trojan commonly associated with the REvil, Egregor, and Black Basta ransomware families. QBot is rapid acting, and capable of stealing data within 30 minutes of a system’s initial compromise. Similar to Emotet, QBot attacks are delivered primarily via email phishing lures. Most recently, QBot attacks are being delivered in thread hijacking campaigns via .lnk files, aiding in its ability to remain undetected.
Bumblebee
In a matter of months, newcomer Bumblebee has become the third most reported payload family, representing 2.9% of attacks in Q2. Bumblebee is a malware loader that was first detected in March 2022. It is delivered via malicious ISO files attached to phishing emails.
Bumblebee is used broadly across various threat groups and is rumored to have been intentionally developed as a replacement to Trickbot and BazaLoader. Bumblebee has so far displayed similar tactics, techniques, and procedures as the Trickbot botnet, and is linked to multiple ransomware varieties including Conti, Quantum, and MountLocker.
Malicious emails continue to be the primary delivery method of payloads aiding ransomware attacks. As security teams implement strategies to detect and disrupt malware campaigns, threat actors modify their behavior and software to increase their odds of success. PhishLabs proactively monitors for email threats to corporate users to better protect organizations from damaging malware attacks.
