Digital Risk Protection (DRP) continues to gain momentum and attention among CISOs and security professionals. DRP, an operational security function once classified under Threat Intelligence (TI), has been elevated by the Gartner Hype Cycle and other analyst research as an emerging security function that security teams rely on to address multiple external cyber threat use cases. Many enterprises get tremendous value from DRP every day, but for those who are unfamiliar, read on to learn what DRP is, how it differs from TI, and how it can help protect your digital assets from external threats.
According to Gartner, DRP solutions are benefitting from significant growth supported by a broad range of needed threat detection and response services. Gartner predicts that “by 2025, the target audience for digital risk protection services will increase to 10%, up from 1% today."[i] This is primarily due to DRP's effectiveness at accelerating both the breadth and depth of protecting digital assets from a variety of external threats. But while DRP adoption continues to grow, some perceived market overlap still exists between DRP and TI and where businesses should focus.
Why Digital Risk Protection?
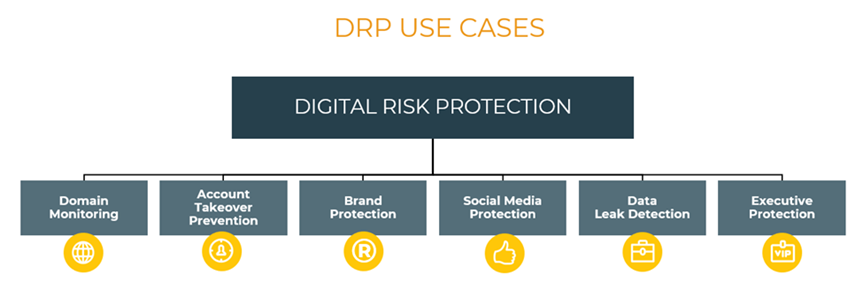
DRP is an operational process that combines intelligence, detection, and mitigates attacks across the external digital risk landscape. While traditional TI gathers intelligence with an eventual end result of using the data to defend internal resources against external threats, DRP focuses on immediately identifying and mitigating the threats that target corporate assets outside the protective walls of your network. As a result, it serves as your first line of defense for monitoring and taking down look-alike domains, avoiding malicious account takeovers, protecting the reputation and integrity of your brand and senior executives, monitoring and protecting against social media threats, and detecting data leaks.
Effective DRP requires a balance of cutting-edge, automated collection and curation technologies combined with expert human analysis to quickly derive value from the massive amount of intelligence required to search for and mitigate the threats that could cripple your business. This operational approach helps detect and quickly mitigate threats to maintain business resiliency.
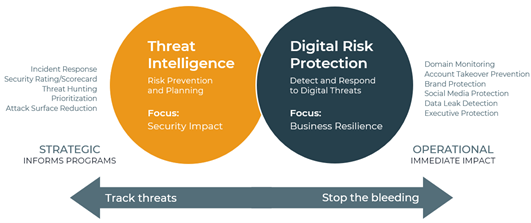
DRP Stops the Bleeding, TI Informs Defensive Programs
While DRP detects and mitigates active external threats to help enterprises quickly stop the bleeding, TI focuses on the methodical process of gathering intel to help predict and prevent threats from impacting internal resources. It includes gathering and analyzing large sets of data over a long period of time to enforce strategic decision making.
TI involves investigative processes designed to determine the overarching security impact potential threats may have on a business, as well as the severity. The goal is to plan and assess the entire landscape of an organization to anticipate potential threats and allocate resources that will ensure optimal security. Common use cases include Incident Response planning, developing security ratings and scorecards to rank threats and determine an organization's preparedness for combatting threats, strategic prioritization of threats, and assessing a businesses' vulnerable attack surface to reduce the overall exposed footprint.
While the process is thorough and labor intensive, it helps businesses with the vision, capabilities, and scope to identify and eventually mitigate threats occurring in real-time. However, while TI is helpful in identifying a universe of threats, it's a partial solution that relies on additional security investments and program maturity to mitigate threats and derive value.
So Which Comes First?
As the evolution of cyber threats stretch security budgets to cover an expanding threat landscape, it's understandable why security teams are constantly grappling with the decision of how to best protect their business. While best practices would suggest that DRP and TI should eventually co-exist as complimentary processes of a comprehensive security program, businesses must first assess their strategic and operational security needs, as well as their threat landscape based on the volume, severity and risk of the cyberthreats that impact them daily to best determine focus and investment.
Traditional TI helps map the strategic threats that could potentially be harmful to an organization over time but is not optimized to efficiently address and mitigate active external threats. Digital Risk Protection is flexible, adaptable, and immediately actionable as a complete solution, providing the operational focus needed to identify and mitigate external threats fast.
An additional benefit of DRP is that it's not dependent on the maturity of your security program or size of business. In fact, depending on the severity of your individual threats, DRP is flexible enough to piece security protection functions together, as needed over time, and continually add functions as your security strategy matures, reducing cost of entry and making it a more manageable process to combatting external threats. Businesses of any size, maturity, and in any phase of security preparedness can quickly derive value from DRP, regardless of the unique external threats they are working to mitigate. Learn more about PhishLabs Digital Risk Protection.
[i] Gartner, Emerging Technologies: Critical Insights in Digital Risk Protection Services, 2 July 2020, Ruggero Contu, and Elizabeth Kim.
Additional Resources: