With many U.S. citizens still waiting to receive their government-mandated stimulus, we are again seeing cyber criminals shift their tactics in accordance with the news cycle. Below is one example of a lure abusing access to an undeliverable stimulus payment.
We are providing ongoing updates on coronavirus-themed attacks observed by the PhishLabs team. This post and others are meant to help the security community stay up-to-date on how threat actors are exploiting the pandemic.
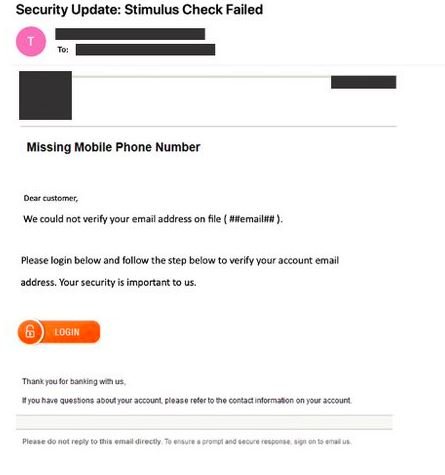
The sender's address is delivered through SendGrid, masking the true IP address.
By clicking the link, the user is directed to hXXps://rlnashracing[dot]com/wp-content/wc-inf/https.{redacted}(dot)com(dot)home/{redacted}-security-update/login(dot)php, a phishing page meant to steal banking credentials.
Threat actors understand that many individuals are eagerly awaiting their stimulus payment. That, combined with the urgent pace of the stimulus payment rollout, creates a prime opportunity for hijacking financial accounts. The IRS recently launching a new program to track stimulus payments online, as well as quicker payments if you provide your banking information instead of waiting for a paper check, are just two examples that, coupled with the stress of financial woes, make stimulus phish very compelling.
For more intelligence on COVID-19 threats, see our ongoing coverage.
